The cybersecurity world faces a fresh challenge as attackers have discovered a weak point in Microsoft Windows SmartScreen. We’ll examine this complex intrusion method, discussing how it works, what risks it poses, and steps you can take to safeguard your systems.

The Vulnerability: CVE-2024-21412
CVE-2024-21412 is a critical flaw in Microsoft Windows SmartScreen that allows attackers to bypass security warnings. This vulnerability opens the door for malicious actors to deliver harmful payloads without triggering the usual security alerts that users rely on for protection
Have you ever encountered a SmartScreen warning? Share your experience in the comments!
The Attack Chain: A Multi-Stage Assault
The attackers have crafted a complex, multi-stage attack that unfolds as follows:
1. The Lure: Users are tricked into clicking a specially crafted link.
2. The Download: This link leads to an LNK file download.
3. The Execution: The LNK file, when opened, downloads an executable containing an HTA script.
4. The Deception: Two files are then downloaded – a decoy PDF and a malicious shell code injector.
5. The Payload: Finally, stealers like Meduza and ACR are injected into legitimate processes.
Can you identify the stages where user interaction is required? How might an attacker exploit human psychology in these stages?
Evasion Techniques: Staying Under the Radar
The threat actors employ various techniques to avoid detection:
– Using low-detection rate image hosting services
– Extracting shell code from image pixels
– Employing multiple types of injectors
– Utilizing “dead drop resolver” techniques to hide C2 servers
What other evasion techniques have you encountered in your cybersecurity experience?
The Targets: A Global Threat
This campaign isn’t limited to a single region. Researchers have observed attacks targeting:
– North America
– Spain
– Thailand
The use of region-specific decoy PDFs suggests a tailored approach to different geographical areas.
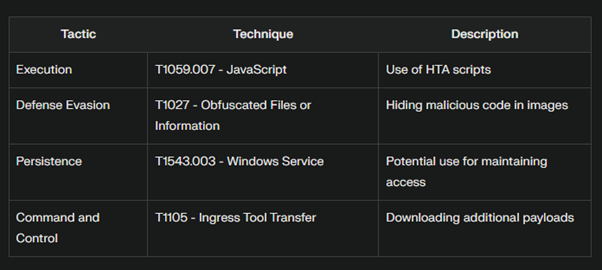
MITRE ATT&CK Matrix: Mapping the Threat
Let’s break down some of the techniques used in this campaign according to the MITRE ATT&CK framework:
Conclusion: Vigilance in a Connected World
1. Keep your systems updated with the latest security patches.
2. Be cautious of unsolicited links and file downloads.
3. Use robust antivirus and anti-malware solutions.
4. Implement network segmentation and monitoring.
5. Educate users about social engineering tactics.
The CVE-2024-21412 stealer campaign serves as a stark reminder of the sophisticated threats we face in our interconnected digital world. By staying informed, implementing robust security measures, and fostering a culture of cybersecurity awareness, we can better protect ourselves and our organizations from these evolving threats.
Remember, cybersecurity is a shared responsibility. Your actions can make a difference in creating a safer digital environment for everyone.
How has this information changed your perspective on cybersecurity? What steps will you take to enhance your digital safety?



