The cybersecurity field constantly faces new challenges as attackers develop creative methods to breach defenses and access confidential data. This discussion examines a recent operation that combines social manipulation tactics and harmful automated scripts to introduce a newly identified data theft tool called “Daolpu.” We’ll analyze this attack strategy to extract valuable insights.

The Lure: A Wolf in Microsoft’s Clothing
On July 22, 2024, CrowdStrike Intelligence uncovered a devious ploy targeting unsuspecting users. The bait? A Word document masquerading as a Microsoft recovery manual. This document, enticingly named “New_Recovery_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.docm,” was designed to exploit the trust users place in official-looking documentation.
Interactive Element: Have you ever encountered a suspicious document at work? What made you question its authenticity? Share your experiences in the comments below!
The Hook: Malicious Macros in Action
Upon opening the document, users unknowingly trigger malicious macros that set the stage for the main act. These macros perform a series of actions:
1. Download a second-stage DLL from a remote server
2. Save it as “mscorsvc.dll” in the system’s temp folder
3. Decode the DLL using the Windows utility “certutil”
4. Execute the decoded DLL using “rundll32”
This intricate process showcases the sophistication of modern malware delivery techniques.
Enter Daolpu: The Stealthy Data Thief
The star of this malicious show is Daolpu, a previously unidentified stealer with a penchant for browser-stored credentials. Once activated, Daolpu gets to work:
– Harvesting sensitive information from web browsers
– Saving the stolen data to a temporary file
– Exfiltrating the collected information to a command-and-control (C2) server
Pop Quiz: Can you name three best practices for safeguarding your browser-stored credentials? (Hint: Think about password managers, multi-factor authentication, and regular security audits)
MITRE ATT&CK: Mapping the Threat
To better understand the tactics employed in this campaign, let’s look at the MITRE ATT&CK matrix:
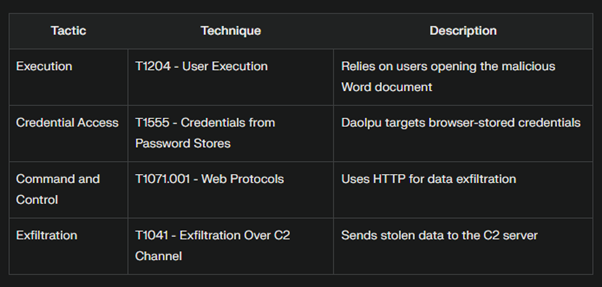
Defending Against the Deception
As cybersecurity professionals, it’s crucial to stay ahead of these threats. Here are some key takeaways and defensive strategies:
1. User Education: Train employees to recognize suspicious documents and email attachments.
2. Macro Security: Disable macros by default and implement strict policies for enabling them.
3. Network Monitoring: Watch for unusual outbound connections, especially those using HTTP for data transfer.
4. Browser Security: Encourage the use of password managers and multi-factor authentication.
5. Regular Updates: Keep all systems and software up-to-date to patch known vulnerabilities.
What additional security measures does your organization implement to protect against similar threats? Share your insights and let’s learn from each other!



